The ISO 27001 certification demonstrates that NeoCheck is committed to the development and ongoing maintenance of an Information Security Management System that will be regularly audited and certified by an independent and external auditor.
“The NeoCheck authentication service provides our customers with flexibility and cost savings, while maintaining the high levels of security required to guarantee access to confidential data and applications” explains Pablo Quevedo, IT Operations and Infrastructure Manager of SUMA Mexico.
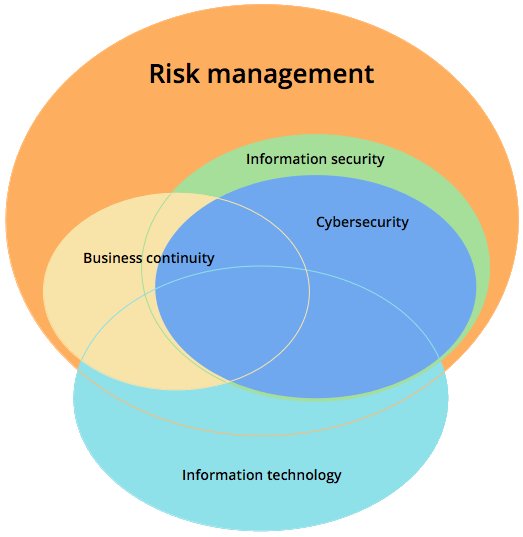
What does ISO 27001 do?
The focus of ISO 27001 is to protect the confidentiality, integrity and availability of the information in a company. This is done by finding out what potential problems could happen to the information (i.e., risk assessment), and then defining what needs to be done to prevent such problems from happening (i.e., risk mitigation or risk treatment). Therefore, the main philosophy of ISO 27001 is based on managing risks: find out where the risks are, and then systematically treat them.
The safeguards (or controls) that are to be implemented are usually in the form of policies, procedures and technical implementation (e.g., software and equipment). However, in most cases companies already have all the hardware and software in place, but they are using them in an unsecure way – therefore, the majority of the ISO 27001 implementation will be about setting the organizational rules (i.e., writing documents) that are needed in order to prevent security breaches. Since such implementation will require multiple policies, procedures, people, assets, etc. to be managed, ISO 27001 has described how to fit all these elements together in the information security management system (ISMS).
So, managing information security is not only about IT security (i.e., firewalls, anti-virus, etc.) – it is also about managing processes, legal protection, managing human resources, physical protection, etc.
How does ISO 27001 actually looks like?
ISO/IEC 27001 is split into 11 sections, plus Annex A. Sections 0 to 3 are introductory (and are not mandatory for implementation), while sections 4 to 10 are mandatory – meaning that all their requirements must be implemented in an organization if it wants to be compliant with the standard. Controls from Annex A must be implemented only if declared as applicable in the Statement of Applicability.
According to Annex SL of the International Organization for Standardization ISO/IEC Directives, the section titles in ISO 27001 are the same as in ISO 22301:2012, in the new ISO 9001:2015, and other management standards, enabling easier integration of these standards.
Section 0: Introduction – explains the purpose of ISO 27001 and its compatibility with other management standards.
Section 1: Scope – explains that this standard is applicable to any type of organization.
Section 2: Normative references – refers to ISO/IEC 27000 as a standard where terms and definitions are given.
Section 3: Terms and definitions – again, refers to ISO/IEC 27000.
Section 4: Context of the organization – this section is part of the Plan phase in the PDCA cycle and defines requirements for understanding external and internal issues, interested parties and their requirements, and defining the ISMS scope.
Section 5: Leadership – this section is part of the Plan phase in the PDCA cycle and defines top management responsibilities, setting the roles and responsibilities, and contents of the top-level Information security policy.
Section 6: Planning – this section is part of the Plan phase in the PDCA cycle and defines requirements for risk assessment, risk treatment, Statement of Applicability, risk treatment plan, and setting the information security objectives.
Section 7: Support – this section is part of the Plan phase in the PDCA cycle and defines requirements for availability of resources, competences, awareness, communication, and control of documents and records.
Section 8: Operation – this section is part of the Do phase in the PDCA cycle and defines the implementation of risk assessment and treatment, as well as controls and other processes needed to achieve information security objectives.
Section 9: Performance evaluation – this section is part of the Check phase in the PDCA cycle and defines requirements for monitoring, measurement, analysis, evaluation, internal audit and management review.
Section 10: Improvement – this section is part of the Act phase in the PDCA cycle and defines requirements for nonconformities, corrections, corrective actions and continual improvement.
Annex A – this annex provides a catalogue of 114 controls (safeguards) placed in 14 sections (sections A.5 to A.18).
Documents we have prepared
ISO 27001 requires the following documentation to be written:
- Scope of the ISMS (clause 4.3)
- Information security policy and objectives (clauses 5.2 and 6.2)
- Risk assessment and risk treatment methodology (clause 6.1.2)
- Statement of Applicability (clause 6.1.3 d)
- Risk treatment plan (clauses 6.1.3 e and 6.2)
- Risk assessment report (clause 8.2)
- Definition of security roles and responsibilities (clauses A.7.1.2 and A.13.2.4)
- Inventory of assets (clause A.8.1.1)
- Acceptable use of assets (clause A.8.1.3)
- Access control policy (clause A.9.1.1)
- Operating procedures for IT management (clause A.12.1.1)
- Secure system engineering principles (clause A.14.2.5)
- Supplier security policy (clause A.15.1.1)
- Incident management procedure (clause A.16.1.5)
- Business continuity procedures (clause A.17.1.2)
- Statutory, regulatory, and contractual requirements (clause A.18.1.1)
And these are the mandatory records:
- Records of training, skills, experience and qualifications (clause 7.2)
- Monitoring and measurement results (clause 9.1)
- Internal audit program (clause 9.2)
- Results of internal audits (clause 9.2)
- Results of the management review (clause 9.3)
- Results of corrective actions (clause 10.1)
- Logs of user activities, exceptions, and security events (clauses A.12.4.1 and A.12.4.3)
